The DES algorithm is a symmetric cryptosystem in the cryptosystem, also known as the US data encryption standard. It is a symmetric cryptosystem encryption algorithm developed by IBM in 1972. The plaintext is grouped by 64 bits, the key length is 64 bits, and the key is actually 56 bits participating in the DES operation (the 8, 16, 24, 32, 40, 48, 56, 64 bits are check digits, so that each key is made The key has an odd number of 1) packetized plaintext group and 56-bit key substitution or exchange method to form a ciphertext group encryption method.
The basic principle of des algorithm
There are three entry parameters: key, data, mode. Key is the key used for encryption and decryption, data is the data encrypted and decrypted, and mode is its working mode. When the mode is the encryption mode, the plaintext is grouped according to 64 bits to form a plaintext group, and the key is used to encrypt the data. When the mode is the decryption mode, the key is used to decrypt the data. In practice, the key only uses 56 of the 64 bits, so that it has high security.
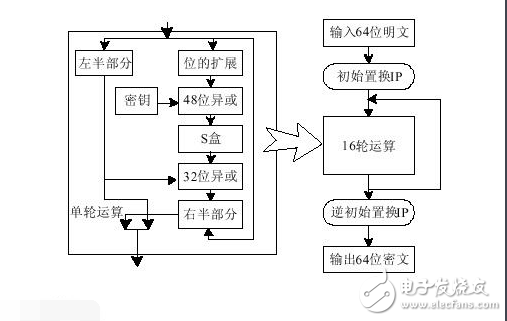
Des algorithm structure
DES features
The DES algorithm is extremely secure. So far, in addition to attacking the DES algorithm with the exhaustive search method, no more effective methods have been found. The 56-bit long key has an exhaustive space of 2^56, which means that if the speed of a computer is one million keys per second, it will take nearly 2285 to search for the full key. The time, it can be seen that this is difficult to achieve. However, this does not mean that DES is unbreakable. In fact, with the development of hardware technology and the Internet, the possibility of cracking is increasing, and the time required is less and less. It takes several hours to process in parallel using specially designed hardware. In order to overcome the shortcomings of the DES key space, a variant of the triple DES has been proposed.
RSA algorithmThe RSA public key encryption algorithm was proposed in 1977 by Ron Rivest, Adi Shamir, and Leonard Adleman. It was first announced in the United States in July 1987, when three of them were working internships at the Massachusetts Institute of Technology. The RSA is composed of the letters of the three names of the three of them.
RSA is currently the most influential and most commonly used public key encryption algorithm. It is resistant to most of the password attacks known to date and has been recommended by ISO as the public key data encryption standard.
Today only a short RSA key can be broken by a powerful method. As of 2008, there is no reliable way to attack the RSA algorithm in the world. As long as the length of the key is long enough, the information encrypted with RSA cannot actually be broken. But today, with the growing maturity of distributed computing and quantum computer theory, RSA encryption security has been challenged and questioned.
The RSA algorithm is based on a very simple theory of number theory: it is very easy to multiply two large prime numbers, but it is extremely difficult to factorize the product, so the product can be exposed as an encryption key.
RSA features
1) It is very troublesome to generate a key, which is limited by the technique of prime number generation, and thus it is difficult to achieve one time and one secret.
2) Security, the security of RSA depends on the factorization of large numbers, but it does not theoretically prove that the difficulty of deciphering RSA is equivalent to the difficulty of large number decomposition, and most people in cryptography tend to factorize not NP. Nowadays, people have been able to decompose more than 140 large prime numbers of decimal digits, which requires longer keys and slower speeds. In addition, people are actively looking for ways to attack RSA, such as ciphertext attacks. The average attacker is Make a message spoof (Blind) and let the entity with the private key sign it. Then, after calculation, you can get the information it wants. In fact, the attack uses the same weakness, that is, there is a fact that the power preserves the multiplicative structure of the input:
(XM)d = Xd *Md mod n
As mentioned earlier, this inherent problem comes from the most useful feature of public key cryptosystems - everyone can use public keys. However, this problem cannot be solved by the algorithm. There are two main measures: one is to use a good public key protocol to ensure that the entity does not decrypt the information generated by other entities arbitrarily during the work process, and does not sign the information that it knows nothing about it; One is to never sign a random document sent by a stranger. When signing, first use One-Way Hash FuncTIon to HASH the document, or use different signature algorithms at the same time. In addition to using public modulo, people also try to exploit attacks such as decryption index or φ(n).
3) The speed is too slow. Because the RSA packet length is too large, n must be at least 600 bits or more for security. This makes the operation costly, especially slower, which is several orders of magnitude slower than the symmetric cipher algorithm. With the development of large number decomposition technology, this length is still increasing, which is not conducive to the standardization of data formats. The SET (Secure Electronic TransacTIon) protocol requires the CA to use a 2048-bit key and other entities to use a 1024-bit key. For speed problems, people use a combination of single and public key cryptography. The advantages and disadvantages are complementary: single-key cryptography is fast, people use it to encrypt long files, and then use RSA to encrypt file keys. Solved the problem of key distribution for single-key cryptography.
The difference between DES algorithm and RSA algorithmRAS: Asymmetric encryption algorithm
The asymmetric encryption algorithm uses two completely different but perfectly matched pairs of keys—public and private. When encrypting a file using an asymmetric encryption algorithm, the encryption and decryption process of the plaintext can be completed only by using a matching pair of public and private keys. Public key encryption is used when encrypting plaintext. The private key can be used to decrypt the ciphertext, and the sender (encryptor) knows the public key of the recipient. Only the receiver (the decryptor) is the only one who knows his private key. people. The basic principle of the asymmetric encryption algorithm is that if the originator wants to send encrypted information that only the addressee can interpret, the sender must first know the public key of the addressee and then use the public key of the addressee to encrypt the original text; After receiving the encrypted ciphertext, the recipient uses its own private key to decrypt the ciphertext. Obviously, with asymmetric encryption algorithm, before the sender and the receiver communicate, the receiver must send the public key that has been randomly generated to the sender, and keep the private key. Since the asymmetric algorithm has two keys, it is especially suitable for data encryption in distributed systems. The widely used asymmetric encryption algorithms are the RSA algorithm and the DSA proposed by the US National Bureau of Standards. Encryption technology based on asymmetric encryption algorithms is widely used.
DES algorithm
The DES algorithm is a symmetric cryptosystem in the cryptosystem, and has become the US data encryption standard. It is a symmetric cryptosystem encryption algorithm developed by IBM in 1972.
The key length is 56 bits, and the plaintext is grouped by 64 bits. The ciphertext group encryption method is formed by replacing or exchanging the grouped plaintext group and the 56-bit key.
DES encryption algorithm features: short grouping, short key, short password life cycle, and slow computing speed.
The basic principle of DES work is that there are three entry parameters: key, data, and mode. Key is the key used for encryption and decryption, data is the data encrypted and decrypted, and mode is its working mode. When the mode is the encryption mode, the plaintext is grouped according to 64 bits to form a plaintext group, and the key is used to encrypt the data. When the mode is the decryption mode, the key is used to decrypt the data. In practice, the key only uses 56 of the 64 bits, so that it has high security.
MicroBT is a technology company which is based on block chain and artificial intelligence. Focusing on integrated circuit chip and products development, production and sales, and provide corresponding system solutions and technical services. We adhere the ideal"ultimate,win-win,integrity"to provide high quality products and service. Now MicroBT has passed the national high-tech enterprise certification.
As a chip design and produce company, completely design process and independent core technology. The core technology include algorithm,fine optimization of integrated circuit micro-structure ,low power technology, advanced chip packaging technology system level power and cooling technology. These core technologies and engineering methods have been successfully validated and applied in the mass production of our block chain server chips and products.
In addition to the current focus on the area of block chains, MicroBT is also responding to the national chip strategy. According to the company's development strategy and plan, MicroBT is planning to explore and extend its core R&D capabilities to other high-performance computing areas such as artificial intelligence through independent R&D and strategic cooperation.
MicroBT Whatsminer:MicroBT Whatsminer M50S,MicroBT Whatsminer M30S++,MicroBT Whatsminer M21,MicroBT Whatsminer D1,MicroBT Whatsminer M30S,MicroBT Whatsminer M10,MicroBT Whatsminer M31S+,MicroBT Whatsminer M20S
Microbt Whatsminer,M30S Microbt Whatsminer,Whatsminer Miner,M50 Miner,Asic Whatsminer
Shenzhen YLHM Technology Co., Ltd. , https://www.hkcryptominer.com